Secure by Design on Oracle: VPD, Data Redaction, TDE, and Role Patterns for Analytics Teams
Hook: Your analysts need row-level access to customer facts, data scientists want masked PII for model training, and auditors demand provable controls—without hand-hacked SQL in every report. On Oracle, you can bake security into the database itself so every query is safe by default.
Why this matters (quick intro)
- Breach blast radius shrinks when policies live in the engine, not in app code.
- Consistent enforcement across SQL*Plus, BI tools, Python, JDBC—because the database enforces rules.
- Compliance-friendly: separation of duties, least privilege, and auditable controls.
This guide gives you a pragmatic blueprint using Virtual Private Database (VPD), Data Redaction, Transparent Data Encryption (TDE), and role patterns specifically for analytics orgs.
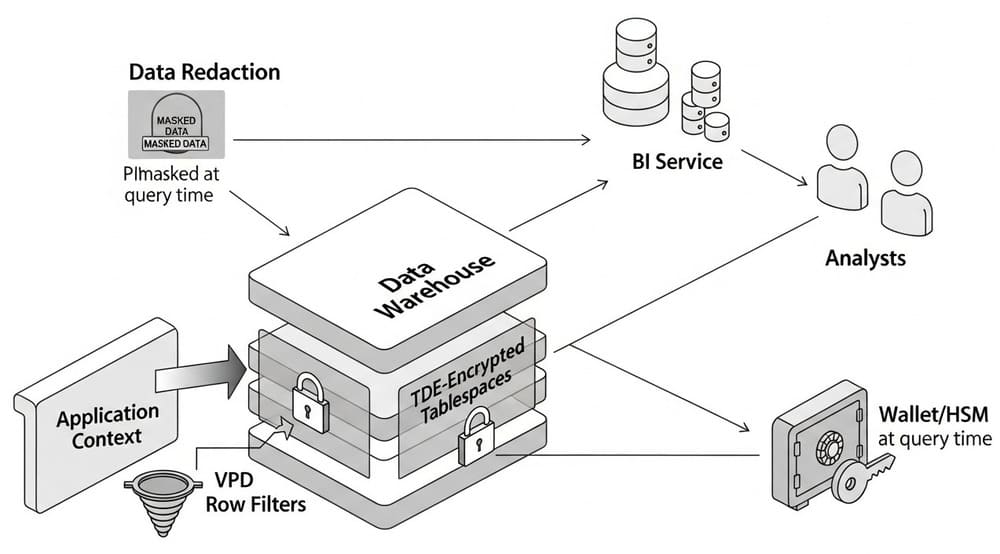
Architecture at a glance
- At-rest: TDE encrypts tablespaces/files; keys managed in a wallet/HSM.
- In-flight: TLS between apps and DB (outside scope here, but required).
- In-use access control:
- VPD (DBMS_RLS) injects a row filter into queries (policy function returns a predicate).
- Data Redaction (DBMS_REDACT) masks columns at query time based on roles/conditions.
- Governance: Roles model personas (Analyst, Data Scientist, BI Service), with break-glass and audit.
Virtual Private Database (VPD): Row-level security that sticks
What it does: On every query (SELECT/INSERT/UPDATE/DELETE), Oracle appends a predicate from a policy function you define.
Common analytics use: Limit visibility by TENANT_ID, REGION, or DATA_CLASS.
Minimal working example
1) Policy function
CREATE OR REPLACE FUNCTION sec.fn_sales_rls (schema_name IN VARCHAR2, table_name IN VARCHAR2)
RETURN VARCHAR2
AS
v_region VARCHAR2(30);
BEGIN
-- e.g., resolve from application context set by mid-tier SSO
v_region := SYS_CONTEXT('APP_CTX','REGION');
IF v_region IS NULL THEN
RETURN '1=0'; -- deny by default
END IF;
RETURN 'region = ''' || REPLACE(v_region,'''','''''') || '''';
END;
/
2) Attach policy to table
BEGIN
DBMS_RLS.ADD_POLICY(
object_schema => 'DW',
object_name => 'SALES_FACT',
policy_name => 'POL_SALES_REGION',
function_schema => 'SEC',
policy_function => 'FN_SALES_RLS',
statement_types => 'SELECT',
update_check => TRUE,
enable => TRUE
);
END;
/
3) Feed the context (app login trigger or mid-tier)
BEGIN
DBMS_SESSION.SET_CONTEXT(
namespace => 'APP_CTX',
attribute => 'REGION',
value => :bound_region -- supplied by mid-tier after SSO
);
END;
/
Good to know
- Multiple dimensions: Add more logic (role + region + dept).
- Performance: Put
REGIONin leading columns of the table/index; predicate must be sargable. - Debugging: Use
DBMS_RLS.ENABLE_POLICY/DISABLE_POLICYand test with different contexts.
Data Redaction: Mask sensitive columns at query time
What it does: Masks or partially redacts values for users who shouldn’t see raw data, while still allowing aggregates.
Typical analytics use: Show last 4 digits of phone or hashed email to analysts; full value only to privileged roles.
Example: Partial and full redaction
BEGIN
-- Phone: keep last 4 digits
DBMS_REDACT.ADD_POLICY(
object_schema => 'DW',
object_name => 'CUSTOMER_DIM',
column_name => 'PHONE',
policy_name => 'RED_PII_PHONE',
function_type => DBMS_REDACT.REGEXP,
expression => 'CASE WHEN SYS_CONTEXT(''USERENV'',''SESSION_USER'') NOT IN (''SEC_ADMIN'',''DS_LEAD'') THEN 1 ELSE 0 END',
regexp_pattern => '(\d{0,6})(\d{4})',
regexp_replace_string => 'xxxxxx\2'
);
-- Email: full redaction unless in privileged role
DBMS_REDACT.ADD_POLICY(
object_schema => 'DW',
object_name => 'CUSTOMER_DIM',
column_name => 'EMAIL',
policy_name => 'RED_PII_EMAIL',
function_type => DBMS_REDACT.FULL,
expression => 'CASE WHEN SYS_CONTEXT(''APP_CTX'',''CAN_VIEW_PII'') = ''Y'' THEN 0 ELSE 1 END'
);
END;
/
Tips
- Condition with context: Drive
expressionfrom application context/roles. - Analytics-safe: Redaction happens after the predicate—aggregations still work, but beware masking skew.
- BI tools: Confirm they don’t cache unredacted data in extracts.
Transparent Data Encryption (TDE): Encrypt at rest without code changes
What it does: Encrypts tablespaces or columns on disk and backups. Queries are unchanged.
Wallet + Tablespace encryption (recommended)
-- Create/open wallet (one-time, paths vary by environment)
ADMINISTER KEY MANAGEMENT CREATE KEYSTORE '/u01/app/wallet' IDENTIFIED BY "Str0ng#Pass!";
ADMINISTER KEY MANAGEMENT SET KEYSTORE OPEN IDENTIFIED BY "Str0ng#Pass!";
ADMINISTER KEY MANAGEMENT SET KEY IDENTIFIED BY "Str0ng#Pass!" WITH BACKUP;
-- Encrypt a new tablespace
CREATE TABLESPACE DW_SECURE DATAFILE '/u02/oradata/dw_secure01.dbf' SIZE 20G
ENCRYPTION USING 'AES256' DEFAULT STORAGE(ENCRYPT);
Notes
- Prefer tablespace encryption over per-column; simpler and covers LOBs, temp, undo if configured.
- Backups (RMAN) remain encrypted—critical for offsite tapes and object storage.
- For HSM/OKV, integrate KMIP-backed wallets for stronger key management and separation of duties.
Role patterns for analytics teams (practical and auditable)
Design roles as personas + capabilities. Keep object grants on roles, not users. Feed contexts via SSO.
Baseline roles
R_ANALYST_READ: SELECT on curated marts + EXECUTE on safe functions.R_DS_READ_WRITE_SANDBOX: Read curated + write into personal/schema sandbox.R_BI_SERVICE: Read + create materialized views in BI-owned schema; no PII by default.R_PII_VIEWER: Grants to view redacted columns unmasked (very limited).R_SEC_ADMIN: Manage VPD/Redaction policies; cannot read business data (separation of duties).R_DDL_OWNER: Owns objects; not used for day-to-day querying.
Example grants
-- Grant read-only mart access
GRANT SELECT ON DW.SALES_FACT TO R_ANALYST_READ;
-- Allow BI to refresh MVs but not see PII
GRANT SELECT ON DW.CUSTOMER_DIM TO R_BI_SERVICE;
-- No grant to EMAIL/PHONE unredacted—redaction handles masking.
-- PII exception with explicit approval
GRANT R_PII_VIEWER TO USER JANE_AUDITOR;
-- Avoid direct to users; assign roles
GRANT R_ANALYST_READ TO USER TEAM_ANALYST1;
Feed application context securely
- Proxy users or mid-tier SSO sets
APP_CTX(region, tenant, PII flag). - Never let clients set context directly; use definer’s rights packages or logon triggers that validate identity.
Putting it together: Example flow for a BI dashboard
- User signs in via SSO → BI service connects as a technical user.
- Mid-tier sets
APP_CTXwithREGION='EMEA',CAN_VIEW_PII='N'. - Queries against
DW.SALES_FACTautomatically getWHERE region='EMEA'from VPD. - Columns like
EMAIL/PHONEreturned redacted to this session. - All data is TDE-encrypted at rest and in backups.
- Access logged via Unified Auditing (enable and review regularly).
Best practices (do this) & common pitfalls (avoid this)
Best practices
- Deny-by-default predicates in VPD when context is missing.
- Index for policy predicates (e.g., composite index
(REGION, PK)), keep predicates sargable. - Separate duties: security admins manage policies; data owners don’t have
SEC_ADMINand vice versa. - Unified Auditing: audit policy changes, role grants, and PII access attempts.
- CI/CD for DDL: version control
DBMS_RLS/DBMS_REDACTscripts; promote via pipelines.
Pitfalls
- Kitchen-sink policies: Huge dynamic predicates hurt the optimizer; prefer simple, cached context values.
- Leaky extracts: Tools exporting to CSV before redaction or from privileged service accounts. Lock them down.
- Column-only encryption: Leaves temp/undo/backups exposed if not also encrypted. Prefer tablespace TDE.
- Grant sprawl: Direct object grants to users become unmanageable; always grant to roles.
- Context spoofing: Never expose
DBMS_SESSION.SET_CONTEXTto untrusted code paths.
Quick comparison table
| Control | Problem Solved | Scope | Overhead | Where It Fails |
|---|---|---|---|---|
| TDE | At-rest encryption | Files, tablespaces, backups | Low | Doesn’t control who sees data after decryption |
| VPD | Row-level authorization | Query predicate | Medium (planning/indexing) | Complex predicates → slow |
| Data Redaction | Mask sensitive columns | Column at query time | Low–Medium | ETL/export jobs with privileged roles |
| Roles | Least privilege & auditability | Users/groups | Admin overhead | Poor hygiene → grant creep |
Real-world snippet: tenant + PII policy combo
-- Context gate
CREATE OR REPLACE FUNCTION sec.fn_tenant_gate(schema_name IN VARCHAR2, table_name IN VARCHAR2)
RETURN VARCHAR2 AS
v_tenant VARCHAR2(36);
BEGIN
v_tenant := SYS_CONTEXT('APP_CTX','TENANT_ID');
RETURN CASE WHEN v_tenant IS NULL THEN '1=0' ELSE 'tenant_id = '''||v_tenant||'''' END;
END;
/
BEGIN
DBMS_RLS.ADD_POLICY(
object_schema => 'DW',
object_name => 'ORDERS',
policy_name => 'POL_TENANT',
function_schema => 'SEC',
policy_function => 'FN_TENANT_GATE',
statement_types => 'SELECT'
);
END;
/
-- Redact card PAN fully unless flagged
BEGIN
DBMS_REDACT.ADD_POLICY(
object_schema => 'DW',
object_name => 'PAYMENT_FACT',
column_name => 'CARD_PAN',
policy_name => 'RED_CARD',
function_type => DBMS_REDACT.FULL,
expression => 'CASE WHEN SYS_CONTEXT(''APP_CTX'',''PCI_OK'') = ''Y'' THEN 0 ELSE 1 END'
);
END;
/
Operational checklist (print this)
- TDE wallet in HSM/OKV, AES256 tablespaces encrypted (incl. TEMP/UNDO if required).
- SSO → mid-tier sets
APP_CTX(tenant/region/PII flags). - VPD policies per sensitive table; deny-by-default when context missing.
- Data Redaction on PII columns; verify BI extracts honor masking.
- Roles by persona; no direct grants to users; quarterly role review.
- Unified Auditing for policy/role changes and PII access.
- CI/CD scripts for DBMS_RLS/DBMS_REDACT with peer review.
- Load tests: compare plan/latency pre/post VPD with realistic predicates and indexes.
Conclusion & Takeaways
- Encrypt by default with TDE to neutralize media loss and backup theft.
- Authorize at the row with VPD so every query is context-aware.
- Mask at the column with Data Redaction to serve analysts without leaking PII.
- Model roles, not one-off grants, and feed application context from SSO to keep policy decisions centralized and auditable.
Implement these four pillars and your analytics platform will be secure by design—not secure by afterthought.
Tags
#Oracle #SecurityByDesign #VPD #DataRedaction #TDE #DataGovernance #Analytics #RowLevelSecurity #PII #DatabaseSecurity





Leave a Reply